When DTLS makes sense. Know before you deploy

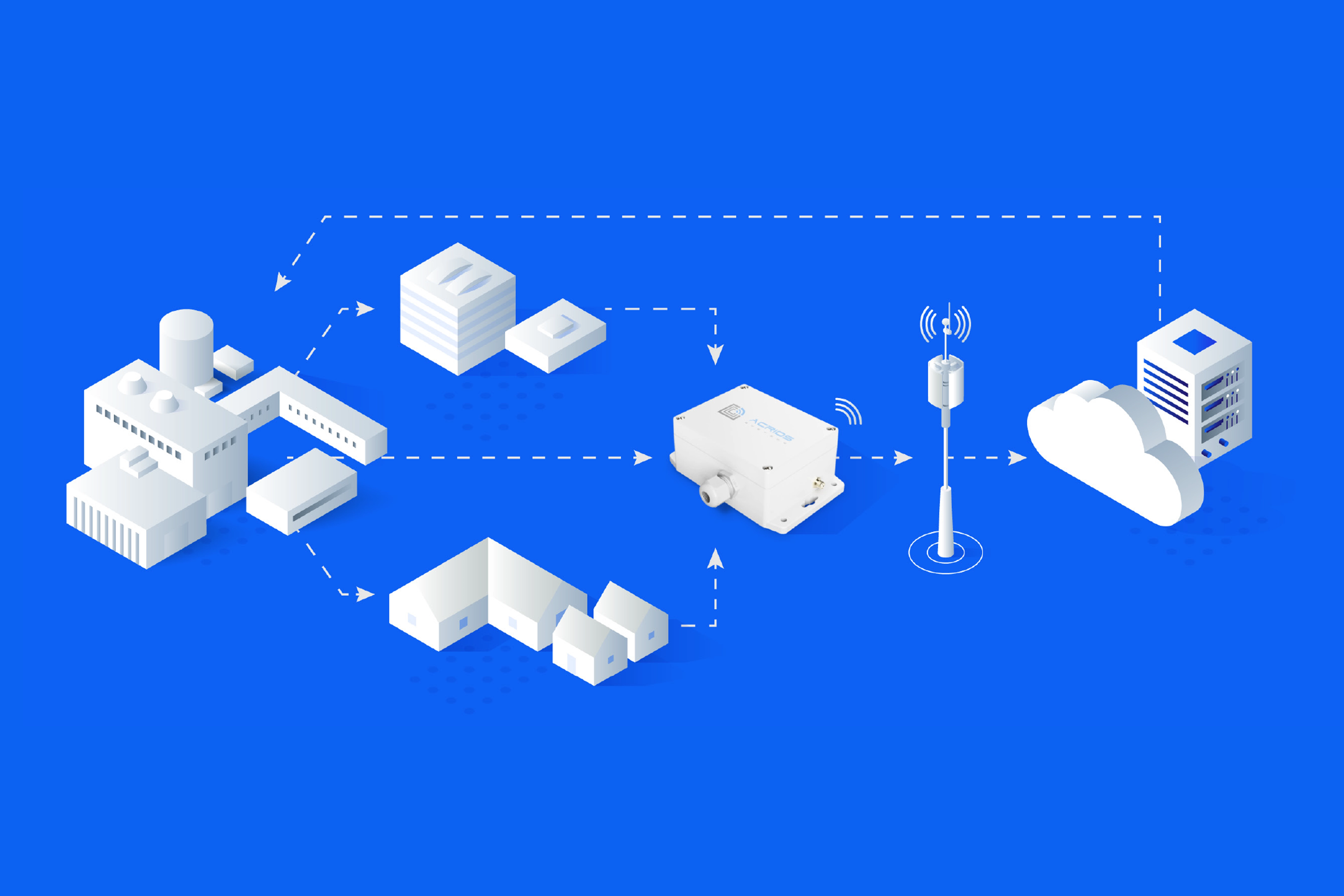
IoT technology is becoming essential across industries, from smart homes to city utilities. Metering infrastructure in particular relies on LPWAN protocols like NB-IoT and LoRa for long-range, low-power wireless communication. But the more sensitive the data, the more important security becomes. Lets explore when DTLS (Datagram Transport Layer Security) makes sense for NB-IoT communication and when it doesn't.
Why secure communication matters
"It’s just water or electricity data, who cares?" you might think. But these seemingly trivial measurements can reveal patterns about personal or business activity: when people are home, what kind of operations are running, or even if there’s been a service disruption. And because many IoT devices communicate over public networks, unencrypted traffic can be intercepted or spoofed by bad actors.
Security isn’t just about protecting your own data. Poorly secured devices can become attack vectors or leak third-party information. In some cases, compromised data can be exploited for market manipulation, industrial sabotage, or targeted attacks.
Security is no longer optional. The EU Radio Equipment Directive (RED) will soon require mandatory cybersecurity features for wireless devices. And the Cyber Resilience Act (CRA), expected to take full effect by December 2027, will bring stricter standards for IoT security and vulnerability management. Encryption will be a key part of compliance.
DTLS: What it is and how it works
DTLS is essentially TLS adapted for UDP. It ensures confidentiality, authenticity, and integrity of data over connectionless protocols. Compared to transport layer VPNs or application-level encryption, DTLS offers:
- Encrypted communication over public NB-IoT networks
- Lower data overhead compared to MQTT with TLS
- Support for identity verification and protection against spoofing
But there are trade-offs:
- Longer handshake times and higher energy consumption
- Greater memory requirements on constrained devices
- More complex key provisioning and management
What are the most common alternatives to DTLS?
- Private APN with UDP. The most basic option. By isolating communication within a mobile operator’s private network, exposure to the public internet is reduced. However, it doesn’t encrypt the data itself.
- MQTT over TLS. Good for cloud integration. TLS ensures end-to-end encryption, but requires more bandwidth and battery power than DTLS. MQTT is also easier to implement and widely supported.
When does DTLS make sense?
DTLS is not a one-size-fits-all solution. It shines in use cases where:
- Public NB-IoT networks are used for transmitting metering data
- Data is privacy-sensitive (e.g., water/gas usage from households)
- Compliance with upcoming EU or national cybersecurity regulations is required
- End-to-end encryption is needed without switching to MQTT
It may not be worth the complexity for:
- Devices with severe power or memory constraints
- Private network deployments with limited exposure
- Use cases where application-level encryption or simpler TLS alternatives suffice
Our recommendation
Start by asking:
- Do I need data confidentiality and identity verification?
- Is my network environment public or private?
- Can my device handle the memory and energy requirements?
We at ACRIOS offer DTLS support in our NB-IoT-enabled converters, as well as MQTT/TLS and private APN communication. Our goal is to help you strike the right balance between security, efficiency, and integration.
FAQs
An IoT device is any internet-connected device that collects, sends, or receives data. Examples include smart meters, thermostats, sensors, or industrial controllers.
No. Devices that process sensitive or time-specific data, such as energy consumption, pose higher security risks, especially when communication is unencrypted.
Unsecured LPWAN networks are vulnerable to data interception, spoofing, and large-scale abuse such as DDoS attacks. Attackers may tamper with data or use unprotected devices as entry points.
Even basic consumption data can be used to infer presence, behaviour, or business operations. Encryption protects privacy and prevents misuse.
It depends on your needs: private APN + UDP for basic isolation, MQTT + TLS for easy cloud integration, and DTLS for efficient encryption over public networks.
Yes. The Cyber Resilience Act and the updated RED directive equire encryption, vulnerability management, and secure default settings from 2025 onwards.
Yes. Even seemingly harmless data can reveal behavioural patterns or be misused for targeted attacks. Operators may also bear liability in case of data leaks.
Consider your energy budget, network type, and integration requirements. ACRIOS supports all major options so you can adapt to your specific project needs.
Yes. All ACRIOS converters support secure communication over LoRa, NB-IoT, and MQTT, with configurable encryption options.
Need to secure your NB-IoT deployment? Our converters support DTLS, MQTT+TLS, and private APN setups. Choose the right option for your project.