Not your keys, not your hardware

It all started with a cipher. In 1997, Belgian cryptographers Joan Daemen and Vincent Rijmen entered a competition held by the U.S. National Institute of Standards and Technology (NIST). Their submission, Rijndael, not only won, it became the basis for what we know today as AES (Advanced Encryption Standard). It was the first publicly available cipher adopted by the U.S. National Security Agency (NSA) for encrypting classified documents.
AES has since become one of the most trusted encryption standards worldwide. Even its “lightest” version, AES-128, is mathematically so strong that brute-forcing it would require 2128 attempts – an astronomical number beyond any real-world threat. At the same time, AES is fast and computationally efficient, which makes it ideal for large-scale use in modern IT and IoT environments.
The weak point of AES? The ownership of the key
Every encryption method has a weak spot. And in the case of AES, it’s the key. It’s the one thing that allows you to encrypt and decrypt your data. If you don’t have access to the key, you don’t have full access to your data either. This is particularly relevant in the IoT world. You may own the physical hardware, but without the AES keys, you depend on whoever holds them. Your data is routed through someone else’s infrastructure, and you have no way to independently verify what’s delivered or who else might access it.
It doesn’t necessarily imply bad intentions. Manufacturers or providers might withhold keys to reduce complexity or manage security risks for less technical users. Still, the result is the same. You lose control over:
- Your data
- Your hardware
- Your choice of service provider
Why owning the AES encryption keys matters
If you do hold the keys, the benefits are substantial. You gain real ownership and control. Here’s what that looks like in practice:
- Direct access to your data: You can independently verify what your device records and control who can access it.
- Freedom to integrate and customise: You’re free to connect the device to your own system, extend its functionality or use it beyond the original ecosystem.
- The ability to switch service providers: You’re not locked into one platform or cloud – change providers when it suits you.
- Stronger negotiating power: When you hold the keys, you set the terms. Not your vendor.
Holding the keys doesn't mean you're on your own
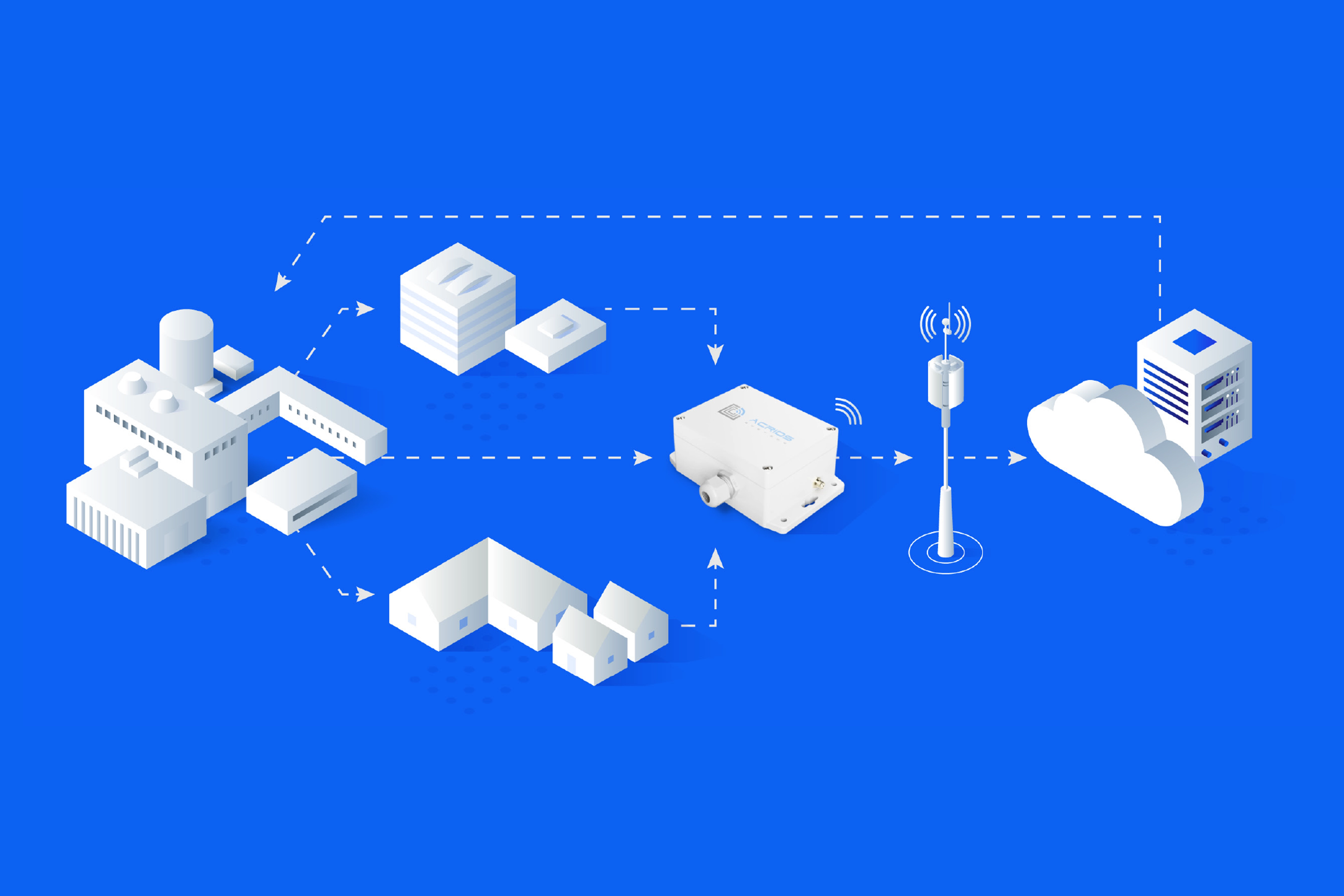
Prefer a fully managed service? That’s fine too. Owning the keys doesn’t mean you're left alone, just that you have a choice. At ACRIOS, we enable AES encryption (AES-CBC and AES-CTR) across all our devices, including wM-Bus and M-Bus converters. Our customers always have the option to keep the keys for themselves. And if they prefer, we can still manage data collection and delivery for them. It’s entirely up to the user.
How to get AES encryption keys for your IoT hardware
Want encryption on your terms? Here’s what to do:
- Check what security options your device supports. AES is the de facto standard. If your hardware doesn’t offer it, look elsewhere.
- Ask for the encryption keys at time of purchase. At ACRIOS, we generate keys as a combination of device ID and message sequence number and we can deliver them directly to the customer.
- Protect your keys. Key security is everything. Whoever holds the key holds access to your data.
FAQs
Not always, but it’s widely adopted and increasingly required by legislation, like the EU Cyber Resilience Act (CRA) or the UK PSTI regulation.
Yes, but you’ll be dependent on your provider’s infrastructure, with no independent access or verification.
Not at all. You can still use vendor-managed services while retaining ownership. It simply gives you more control and flexibility.
Want full control over your encrypted devices? We’ll help you get started. Ask us about our AES-encrypted converters and how you can own the keys.